
This is a summary taken from Judicium’s DPO ‘Sofa Session’ from the 23rd of February, with Data Services Manager William Blanchard, LLM (Hons), L.P.C., PC.dp GDPR. This session was focused on: threats and vulnerabilities, GDPR security standards, GDPR incident reporting, and common pitfalls.
What are the threats and vulnerabilities to schools regarding cyber security?
Ransomeware
We have seen a significant growth in cyber criminality in the form of high-profile ransomware campaigns over the last year. Breaches leaked personal data on a massive scale leaving victims vulnerable to fraud, while lives were put at risk and services damaged by the WannaCry ransomware campaign that affected the NHS and many other organisations worldwide.
Tactics are currently shifting as businesses are targeted over individuals and although phishing attacks on individuals are increasing, fewer are falling victim as people have become more alert.
Cyber Criminals
Because the distinction between nation states and criminal groups is increasingly blurred, cyber-crime attribution is sometimes difficult. Many Russian-speaking cyber groups are threatening UK interests, but home-grown cyber criminals are becoming more sophisticated and therefore a rising threat. Although young criminals are often driven by peer kudos rather than financial reward, organised UK cyber-crime groups are motivated by profit.
Digital Connectivity
In an age of ever-increasing digital connectivity, the threat landscape continues to widen for organisations, heightening the risks of being subject to cyberattacks.
The Pandemic
It has had a major impact on many organisations as workers processing sensitive information have left their controlled work environments to undertake the same work at home, a less regulated and controlled environment.
The Internet of Things (IoT)
The Internet of Things (IoT) and the rise of large, connected networks within homes and places of work, provides attackers with many more end points and options to access networks.
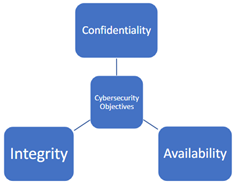
The CIA Triad
A method of categorising the priorities of cyber security. These are relevant to the securing of organisational assets (digital and physical) as well as ascertaining the sufficiency of current safeguards (i.e. are current measures sufficient to ensure C/I/A in the event of a breach).
-
Confidentiality – different from the legal interpretation concerning law of confidential information. This is about ensuring an appropriate level of secrecy is maintained throughout any processing.
-
Integrity - is concerned with ensuring the accuracy, completeness and reliability of information and IT infrastructure.
-
Availability - information and systems must be capable of being accessed reliably and in a timely fashion to those with authorised access.
What can I do?
-
Making sure cyber security is part of your school’s objectives and risks.
-
Make sure cyber security sits with both your DPO and IT departments.
-
Supporting your school leaders to put precautions in place.
-
Holding your school leaders to account to make sure they have systems in place to keep your school secure.
You can do this by:
-
Adding cyber security as an agenda item for your next SLT meeting and your governors meeting.
-
Look at adding cyber security to your school improvement plan (SIP).
-
Checking that cyber security is included as part of your school’s risk register.
-
Give staff training. To see Judicium’s GDPR and cyber security training, please click here.
-
Asking questions.
How do we report a cyber-crime incident?
There are three stages to reporting a cyber-crime incident.
1. The ICO: It is the Information Commissioner’s Office and is in charge of regulating the processing of data in the UK. They provide guidance based off of two key pieces of legislation: the Data Protection Act 2018 and the UK GDPR, as well as the most up to date relevant case law.
2. The Police Cyber-Crime Unit: These are affiliated with your local police service in your area. For example, in and around London there are two cyber-crime units – the Metropolitan Police and the City of London Police.
3. Action Fraud: It is the UK’s national reporting centre for fraud and cybercrime where you should report fraud if you have been scammed, defrauded or experienced cyber crime in England, Wales and Northern Ireland.
There are a few other relevant agencies that can help with reporting cyber-crime, including: The National Crime Agency, The National Cyber-Crime Unit (NCCU) and GCHQ.
What are some common cyber-security pitfalls?
-
Unpatched software: failure to regularly update systems and software can leave weaknesses which are exploited by threat actors.
-
Unencrypted data: unencrypted data increases risk in the event that data is accessed and breached. Data being useless, or at least in a form which cannot be understood when encrypted. This measure is explicitly listed under Article 32 UK GDPR and it expected of all organisations.
-
Misconfigurations: where systems and networks configurations are not understood, opening them up to exploitation.
-
Weak user credentials.
-
Zero-day attacks: an unforeseen vulnerability which was not anticipated by software developers or users.
-
Malicious insider: When someone with internal knowledge of a company’s system utilises or extorts data for malicious means, e.g., Andrew Skelton/Morrisons case.
-
Staff training: employees often pose the greatest risk to an organisation when untrained. Human error is a common pathway for cyber criminals to capitalise on an organisation’s vulnerabilities.
-
Phishing
-
Absence of access controls: without access controls (permissions).
Key Points to Take Away:
-
Consult your DPO immediately if you have been breached or attacked.
-
-
Make sure that you report the incident to the relevant authorities as soon as if possible (Don’t forget the 72-hour window to report to the ICO).
-
-
Take preventative measures now.
-
-
The key route cyber-criminals use to successfully attack an organisation is outdated software on staff computers and laptops.
-
It is imperative that staff update their software when prompted to ensure that the best security measures are in place.
-
-
Encourage staff to have complex passwords.
-
-
Passwords don’t need to be changed regularly if staff all have sufficient protection. Passwords should be at least 8 digits long with a mix of lower and uppercase letters, numbers and symbols.
-
-
Train staff on what to look out for.
-
-
Phishing scams are an easier way to access your computer systems.
-
If in doubt, before opening a suspicious email, contact your IT/ICT provider and ask them to review it.
-
-
Make sure that you have back-ups of any data.
-
-
Back-ups should not be saved on the same server. It is preferable to have your data backed up on a separate server to your hard drive.
-
We have seen a spike in legal action taken against schools that have been breached by cyber-attacks.
This is when your DPO can help. They are there to advise you immediately on any action that may need to be taken as soon as you fear that you have suffered an attack. They will assist you in dealing with the ICO and act as a conduit with them to report your breach and with any steps that they may suggest you take.
Also, we recommend you provide additional training to all staff on data protection in the workplace, how to spot potential threats and in some instances, how to combat them.
Helpful Information:
Questions Governors can ask:
- Tell me about what precautions you have in place to make the school more secure?
- How do you monitor whether the systems our school has in place are effective?
- How often do staff receive training in cyber security?
- What does this training cover? How do you know it's effective?
- What cyber expertise do we need, and what do we already have?
- How do you back up the school's data? Are you confident it would remain unaffected if we had a ransomware attack?
- When did you last organise an audit which looked at cyber security specifically?
- Do you have an incident response plan in place? Is it up to date? How do you know it's effective?
- Do you know who to contact if our school becomes the victim of a cyber incident?
- What does our school do to encourage a good security culture?
- How do you keep track of all the systems and data that you're responsible for?
Links:
UK GDPR - https://uk-gdpr.org/
Data Protection Act 2018 - https://www.legislation.gov.uk/ukpga/2018/12/contents/enacted
ICO - https://ico.org.uk/
Action Fraud - https://www.actionfraud.police.uk/
If you would like more information of how we can support you or more information regarding our DPO service, please see more details regarding the service here.
If you’d like to review Judicium’s forthcoming sofa sessions please click here
Related content
.png)
This is a summary taken from Judicium’s DPO ‘Sofa Session’ from the 11th February, with our Data Protection consultant, Shaafah Mohamed. This session explored the use of CCTV within school settings and its link to data protection. Why CCTV is considered privacy intrusive, the legal basis for its use under UK GDPR, and practical steps schools should take to ensure compliance.

This is a summary taken from Judicium’s DPO ‘Sofa Session’ from the 12th December, with our Data Protection Consultant Daniel Richardson.
This is a summary taken from Judicium’s DPO ‘Sofa Session’ from 22nd October, with our Data Protection Consultant Jessica Vannan. In this session, we broke down what constitutes a data breach, how it should be assessed, and what effective breach management looks like.

This is a summary taken from Judicium’s DPO ‘Sofa Session’ from 24th September, with our Data Protection Consultant Thomas Wynne.
.png)
As Multi-Academy Trusts continue to grow in size and complexity, the responsibility of managing data protection effectively, and legally, has never been greater.

This is a summary taken from Judicium’s DPO ‘Sofa Session’ from 7th May, with our Data Protection Consultant Lane Baker.

Sofa Sessions | Data Protection