Data Breach Alert: No system is Safe - But Your Response Can Be
This is a summary taken from Judicium’s DPO ‘Sofa Session’ from 22nd October, with our Data Protection Consultant Jessica Vannan. In this session, we broke down what constitutes a data breach, how it should be assessed, and what effective breach management looks like.
Case Study: Kido Nursery Chain Data Breach (September 2025)
In September 2025, hackers targeted Kido, a nursery chain with 18 sites in and around London, stealing sensitive data belonging to around 8,000 children—including names, photos, addresses, and safeguarding notes. The attackers claimed to have accessed details of parents and carers and even contacted families directly to extort a ransom.
Kido responded quickly, informing parents and cooperating with the Metropolitan Police and ICO, but the damage was already done. Samples of the stolen data appeared on the dark web, underlining how devastating even a single breach can be when personal data isn’t fully protected.
This case highlights a critical truth: no system is immune, but strong data governance and preparedness, make all the difference.
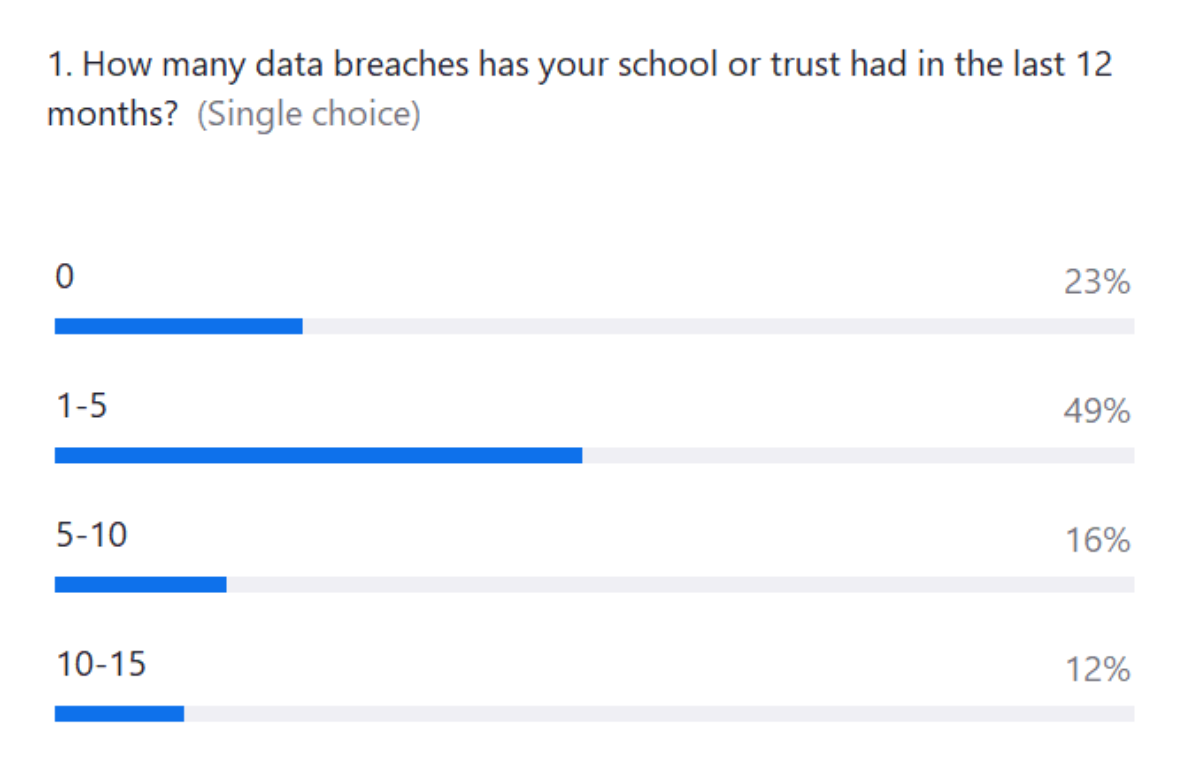
Poll 1
What is a Data Breach?
A personal data breach is the loss, alteration, destruction, unauthorised access and disclosure of personal data.
What Constitutes Personal Data?
To be considered personal data, the information must relate to a person and identify them directly or indirectly.
Examples of Personal Data:
- Full name
- Address
- Email address
- Phone number
- Date of birth
- Photographs or video footage
A data breach occurs when the security of personal information is compromised, potentially resulting in:
- Loss of Data – For example, misplacing a USB drive that contains personal information.
- Destruction of Data – Such as accidentally or deliberately deleting records that hold personal data.
- Alteration of Data – Modifying personal information without proper authorisation, whether intentionally or by mistake.
- Unauthorized Disclosure – For instance, sending personal data to the wrong person by email or post.
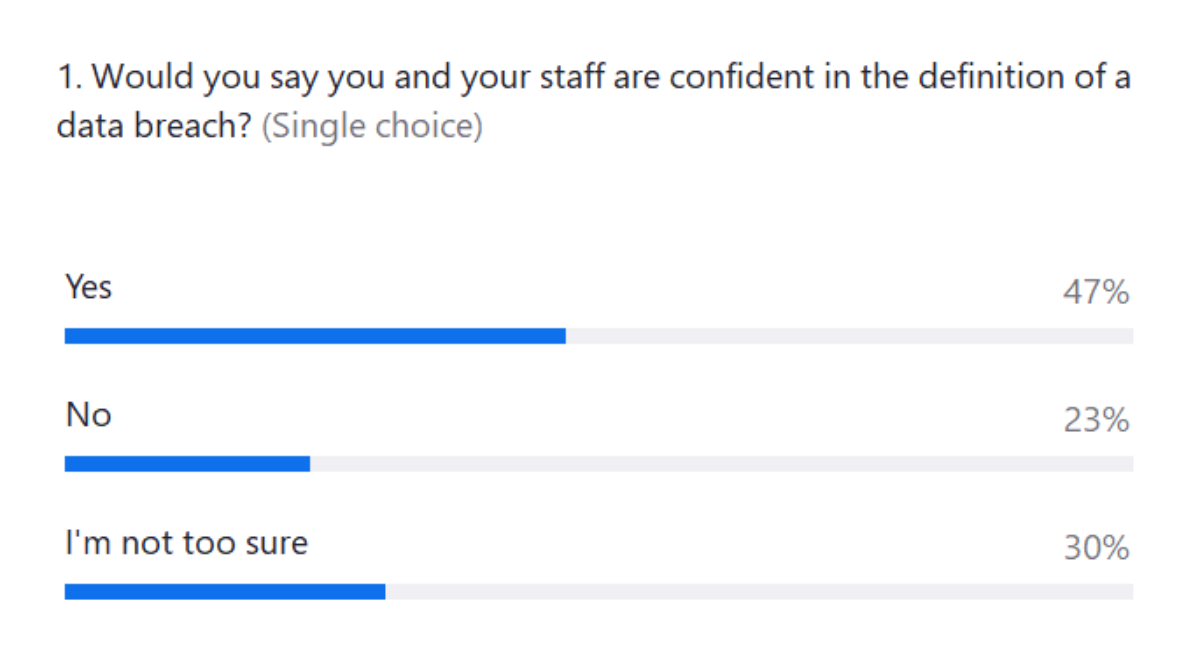
Poll 2
Managing and Accessing a Data Breach
Under UK GDPR, schools have a legal responsibility to manage personal data breaches appropriately. Therefore, should a breach occur, its important to know how to handle it. All staff members should be aware of how to report a breach which is why a Data Breach Policy is important to ensure individuals know their role in managing a breach.
When a Breach Occurs, What Do You Need To Do?
Step 1:
Report the concern to your line manager or the schools designated data protection contact immediately.
Step 2:
The Data Protection Lead (or the individual designated with managing data protection) should notify the Data Protection Officer (DPO). Together, they will assess whether a personal data breach has occurred.
Step 3:
Whilst reporting the breach to your DPO, it is important to investigate the cause of the breach and take prompt action to contain it—this may involve stopping further loss, preventing unauthorised access, or recovering compromised data. Acting quickly here may reduce the likelihood of the breach requiring to be reported further.
Step 4:
Assess the potential risk to individuals affected by the breach. Based on this assessment, the DPO and school must determine whether the incident is reportable to the Information Commissioner’s Office (ICO).
Step 5:
Record all details of the breach in the school’s data breach log. This supports accountability, helps identify patterns or weaknesses, and informs future training needs.
How Would Your DPO Access The Breach?
There are two factors to consider when assessing a breach. Each data breach must be evaluated individually, as the impact can vary depending on the circumstances. For example, a seemingly minor incident, such as sending personal data to the wrong recipient, may initially appear low-risk, but further investigation could uncover factors that significantly increase the risk to individuals. It is always important when assessing the breach that you are looking at the full picture.
The two factors are:
1. Likelihood – e.g., is there likelihood that risk will occur?
2. Severity – e.g., should the risk happen, the seriousness of the consequences.
When assessing a breach, the focus should be on the potential of harm or damage to the affected data subjects. The consequences of a breach can range widely from minor inconvenience to serious emotional, financial, or reputational harm.
Some breaches may pose little or no risk, while others may require urgent action and notification to further parties.
Mitigating Measures
The likelihood of a breach can be reduced by measures being put in place.
- Policies and Processes - Having documents such as a data breach policy detail the process, so a school can handle any breach that occurs.
- Day-to-day reminders and awareness - Reminding staff of the basics.
- Breaches can occur when you least expect it - Ensure data is kept secure to reduce the smallest of breaches.
- Sharing breaches that have occurred with staff - Spreads general awareness that the simplest of mistakes can happen.
- Encouraging a positive culture – Easier when it comes from a staff member rather than the ICO or a member of the public (like a parent) so you are always on the front foot.
- Annual data protection audits with your DPO – This is a great time to assess where the school is at in terms of Data Protection. Your DPO will advise and provide guidance on best practice, and ensure that you are complying with data protection legislation.
- Training – Training is a key element of reducing the risk of data breaches. All staff should carry out data protection training no matter what job they have within the school. Training should be annually to ensure the knowledge is up to date with the latest risks. This may be in the form of face-to-face training and/or online training.
- Cyber Security training - A key training element that supports understanding of data breaches.
Judicium offer eLearning packages and on-site training for data protection training for all staff in school and Governor specific modules. Browse our catalogue here .
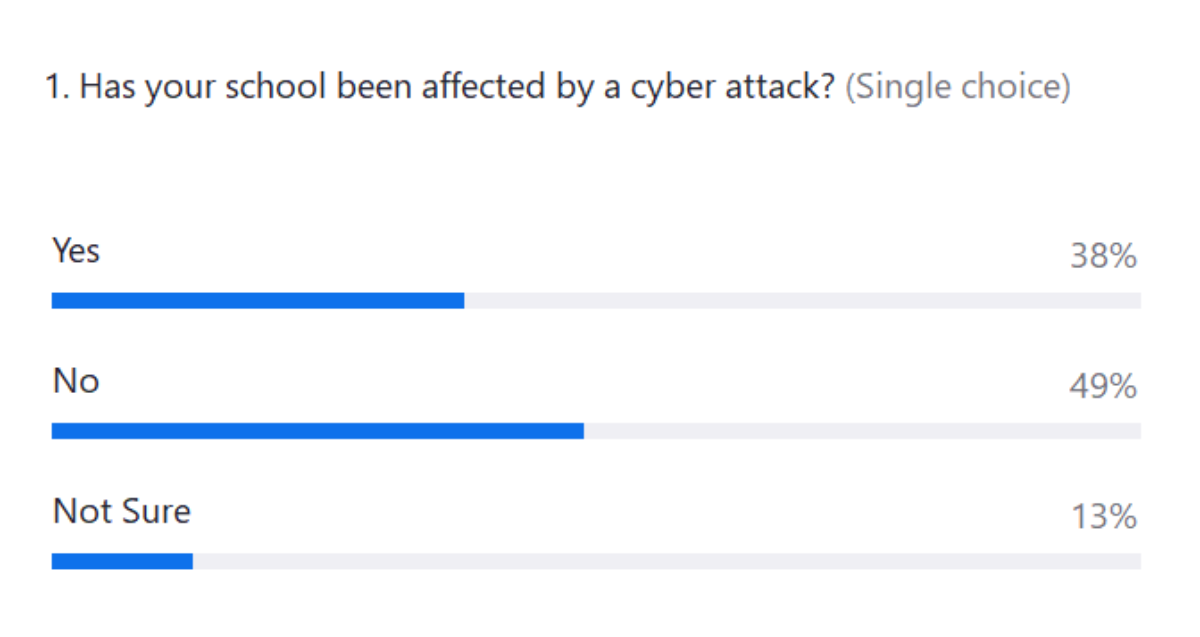
Poll 3
The Rise in Cyber Attacks
Unfortunately, there has been a significant rise in cyber-attacks, with many schools affected by various forms of attack.
The two most common types are:
Malware – Malicious software designed to damage or gain unauthorised access to systems.
Phishing – Fraudulent attempts to obtain sensitive information by impersonating trusted sources.
These attacks often result in personal data being accessed, lost, or stolen, which may constitute a data breach under UK GDPR.
We as a Data Protection service, are being made aware more and more of cyber attacks. In recent circumstances, there have been serious financial implications and reputational damage on schools when a cyber attack has occurred.
If a cyber-attack occurs, the first step is the same as any data breach—contact your DPO and security team immediately. They will help assess the situation, minimise risks to individuals, and determine whether the breach needs to be reported to other authorities such as:
- Information Commissioner’s Office (ICO)
- Police
- Action Fraud Team
- National Cyber Security Centre (NCSC)
At Judicium, we are seeing the ICO take a more detailed approach to investigating these incidents. It is therefore essential that schools can demonstrate their compliance with data protection obligations.
Key Points to Takeaway
Maintain a Data Breach Log.
Ensure that all data breaches, regardless of severity, are consistently recorded in a central log. This helps track incidents and supports accountability.
Empower staff to speak up.
Promote an environment where staff feel safe and supported in raising concerns or reporting potential data breaches, without fear of blame or repercussions.
Designate a Clear Point of Contact.
Assign a specific individual within the school as the go-to person for data protection matters, including breaches. This ensures staff know exactly who to approach and encourages timely reporting.
Implement a Data Breach Policy.
Confirm that your school has a formal data breach policy in place. It should clearly outline procedures, name the Data Protection Officer (DPO), and identify the internal contact responsible for data protection.
Lastly, don’t panic! There are no concerns that are too small to discuss when it comes to a data breach.
How Judicium can help...
You can find information regarding our School Data Protection Officer (DPO) service here.
Jedu is Judicium's online GDPR compliance tracking software for schools. Our platform is suitable for single schools to large MATs and is designed to assist schools with two critical needs: To enable trustees, Governors and other SLT to monitor GDPR compliance; and to assist you managing your data protection.
If you would like more information on how we can support you or more information regarding Jedu, please get in touch with us.
If you require any support in any of these steps or would like to talk to someone surrounding some support for your school, please do not hesitate to call us on 0345 548 7000 or email georgina.decosta@judicium.com.
Follow us on Twitter: @DPOforSchools and @JudiciumEDU
© This content is the exclusive property of Judicium Education. The works are intended to provide an overview of the sofa session you attend and/or to be a learning aid to assist you and your school. However, any redistribution or reproduction of part or all of the contents in any form is prohibited. You may not, except with our express written permission, distribute or exploit the content. Failure to follow this guidance may result in Judicium either preventing you with access to our sessions and/or follow up content.
Related content

This is a summary taken from Judicium’s DPO ‘Sofa Session’ from the 12th December, with our Data Protection Consultant Daniel Richardson.

This is a summary taken from Judicium’s DPO ‘Sofa Session’ from 24th September, with our Data Protection Consultant Thomas Wynne.
.png)
As Multi-Academy Trusts continue to grow in size and complexity, the responsibility of managing data protection effectively, and legally, has never been greater.

This is a summary taken from Judicium’s DPO ‘Sofa Session’ from 7th May, with our Data Protection Consultant Lane Baker.
.png)
A practical guide to help UK schools respond to cyber-attacks, meet legal obligations, and strengthen their overall cybersecurity resilience.
.png)
This is a summary taken from Judicium’s DPO ‘Sofa Session’ from 2nd of April, with Helen King and Sofia Mastrangelo. This session focused on the guidance on sharing safeguarding data and concerns, retention rules, and managing SARs in relation to safeguarding and considering exemptions.

Sofa Sessions | Data Protection